Security Overview
Lumos Controls takes our user’s security and privacy very seriously. We strive to be transparent about our security infrastructure and follow the industry’s best practices. We have a multi-tier security architecture that allows comprehensive security at all platform levels starting from connected devices, applications to cloud infrastructure. The base of our solution is a unique Location-Aware IoT (Internet of Things) platform called ARIXA, which enables smart Lighting, wireless controls, and cloud-based building management reports. It is a highly scalable and secure platform that is designed to address our customer’s scaling needs while allowing seamless interaction between our devices, web, mobile application, and cloud infrastructure.

The base of our solution is a unique Location-Aware IoT (Internet of Things) platform called ARIXA, which enables smart Lighting, wireless controls, and cloud-based building management reports. It is a highly scalable and secure platform that is designed to address our customer’s scaling needs while allowing seamless interaction between our devices, web, mobile application, and cloud infrastructure.
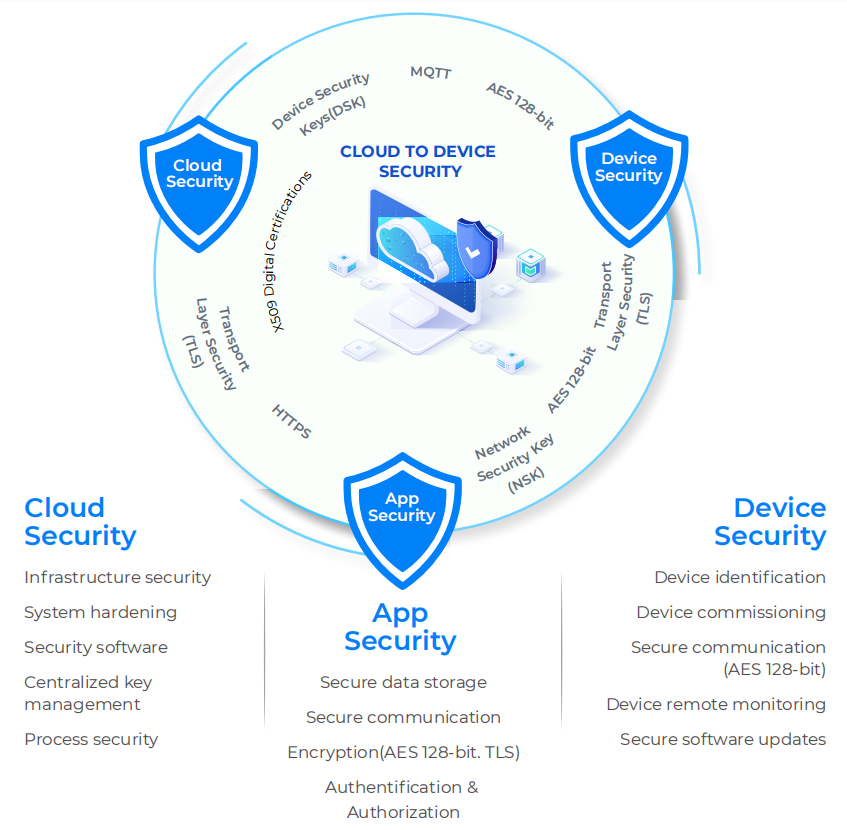
End to end Security
For us, multi-tier security starts when a device is manufactured. During the manufacturing process, every device is embedded with 2 unique, non-repetitive key that allows for secure device identification. The next layer of security is added during the commissioning process when the same devices is programmed and installed using a separate set of keys called Network Security Keys for further encapsulation. All the
communication and key exchange are sequenced to enhance the security further, and the needed validation checks are performed over a highly secure AES 128-bit encrypted network. This approach allows us to prevent the 3R security issues of Readability, Repeatability, and Replaceability. Now let us look in detail at how it is done.

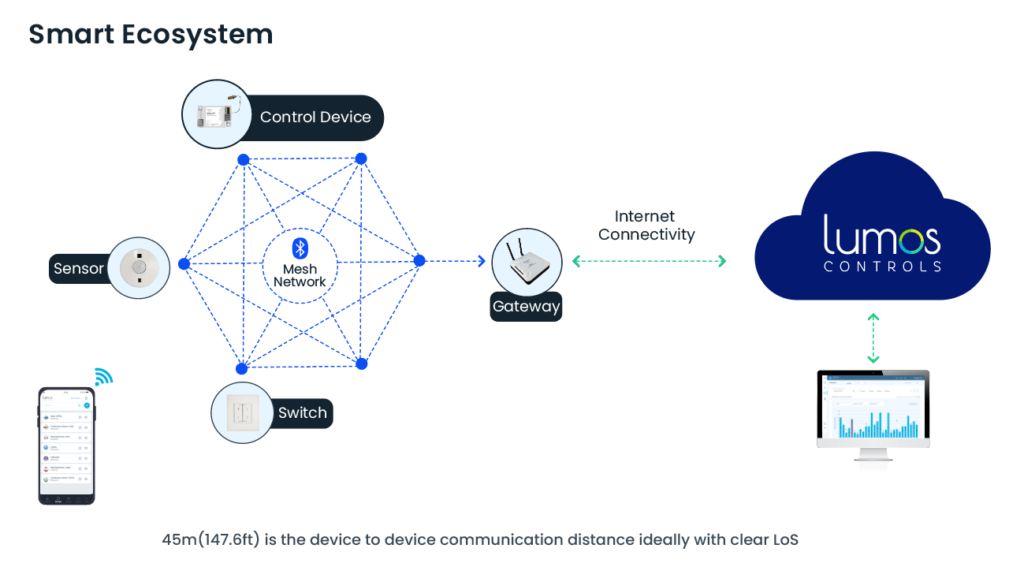
We are a networked lighting control solution with devices communicating over a secured wireless mesh-based network. These devices are provisioned with secured identification keys called Device Security Keys (DSK), which allows for secure communication between the cloud infrastructure and the devices. Furthermore, the transmission is encrypted via AES 128-bit keys. This helps counter against eavesdropping by unintended parties, thereby stopping hackers from data sniffing. For example, when a user uses our mobile application to turn on a lighting fixture, the mobile application sends a request to nearby devices. These requests are encrypted using AES 128-bit encryption and are being confirmed at the device level.

Our solutions are hosted on the highly secure Amazon AWS EC2 cloud. It allows our solutions to be protected by the industry’s best security practices. In addition, all system access is via secured APIs that prohibits direct access to the applications or the database. Cloud security is further enhanced via public key infrastructure (PKI), encrypted user credentials, regular mitigation scanning, web server, and OS hardening. All these come together to make a highly secure IoT ecosystem and prevent replay attacks by hackers.
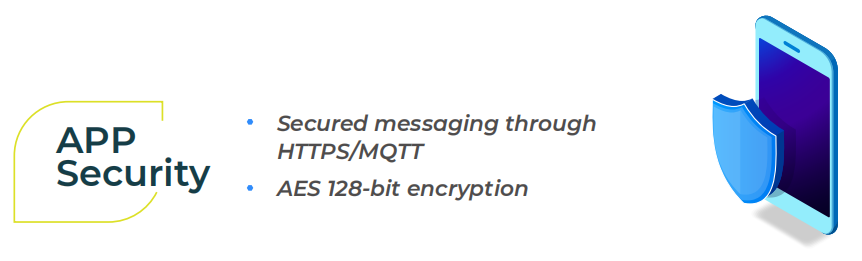
Our user interfaces like mobile and web applications act as a bridge between the devices and the cloud infrastructure. The mobile application is designed to allow commissioning, control, and configuration of the lighting network. The communication between the mobile application and the cloud infrastructure happens securely over HTTPS/MQTT, and the server is programmed to only accept TLS connectivity for authentication and authorization. All this means that the stored data and analytics can only be accessed with the right user authentication, implying that all the sensitive information is safe within the server, thereby countering replaceability.
Secured as Always
Lumos Controls is trusted all over the globe and is used in major commercial buildings and industrial infrastructures like hospitals, hotels, warehouses, retail shops, offices, and many other security-sensitive applications.